Violent Crime to Cybercrime
In his post, Detective Ritch describes Evolution of Facts over the course of a shooting investigation. In this installment we’ll examine how we’ve adapted that paradigm into InfoSec investigations.
Importance of Evolution
Evolving data into higher level objects serves two critical purposes: noise reduction & translation.
Noise Reduction
First, the nature of evolution discards noise. Much like the concept in biology, only fit, useful facts survive the evolution process. When exposed to more complex systems, noise goes the way of the dodo bird. A “possible SQL injection attack on MySQL” event becomes irrelevant when vulnerability reports show the targeted server isn’t running MySQL. As data becomes a more mature, evolved object the irrelevant events fall away.
Translation
The main question facing an incident responder when presented with an event is “How does this impact my organization?” Getting from a single event to a paragraph that the Board of Directors can understand takes significant evolution of the data.
Applying Law Enforcement Vernacular
The mission of WitFoo is to mature the craft of Incident Response. A core hypothesis held is InfoSec is immature because it is using untested, immature paradigms. We test this hypothesis by examining more mature crafts like Law Enforcement.
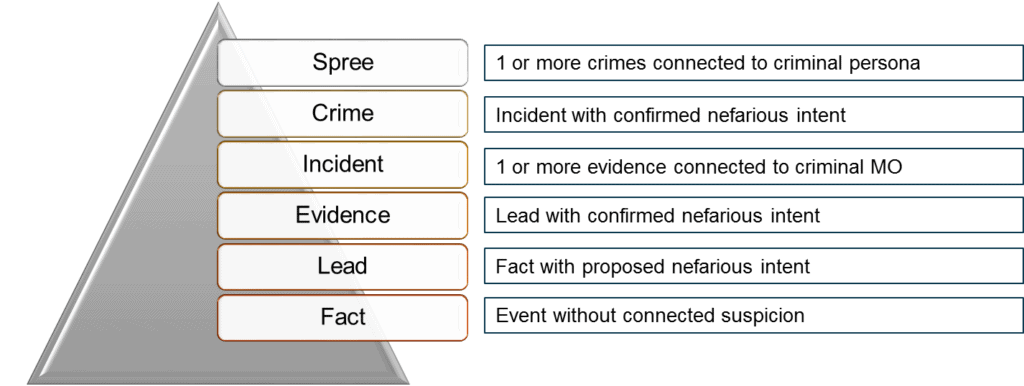
Facts
In InfoSec, a fact is any logged observation. It is often referred to as an artifact by incident responders. Examples of facts are log entries, NetFlow records, packet captures, files and video recordings.
Lead
When a fact has been identified as possibly nefarious, it is promoted (evolved) into a lead. A packet capture that matches a signature for SQL Injection creates a lead that we normally call an event.
Evidence
When a lead is validated as nefarious by an investigator (or system criteria) it is promoted to evidence. This evolutionary step generally requires querying other data sources (i.e. identity logs or reputation feeds).
Incident
When one or more pieces of evidence are connected to the modus operandi (MO) of an aggressor, it is promoted to an incident. In information security, this is generally defined by models like Lockheed’s Cyber Kill Chain or MITRE ATT@CK Continuum. Incident tracking requires evidence over time to be stitched together. It is at this level that human conversations can begin beyond InfoSec professionals.
Crime
When an incident is investigated and determined to be benign, it is called a false positive in InfoSec. It is called an acquittal or dismissal in Law Enforcement. If the intent is confirmed nefarious, the incident is promoted into a Crime. It is at this point that the adversary and motive is identified and the impact to the business is documented.
Spree
When an adversary is connected to multiple crimes, it is known as a Crime Spree in law enforcement and sometimes called a campaign in InfoSec. These are very hard to detect because the victims are distributed (across an industry or geography.)
Application of Vernacular
Evolving data is the work of the investigative craft. Often frustration with executives is born of inadequate data evolution. That inadequacy is caused by lack of tools, process and people (see: Failure Reports.) Starting with an understanding of what the evolutionary steps are can help a Security Architect and IR Team lead craft better approaches in solving this systemic problem.